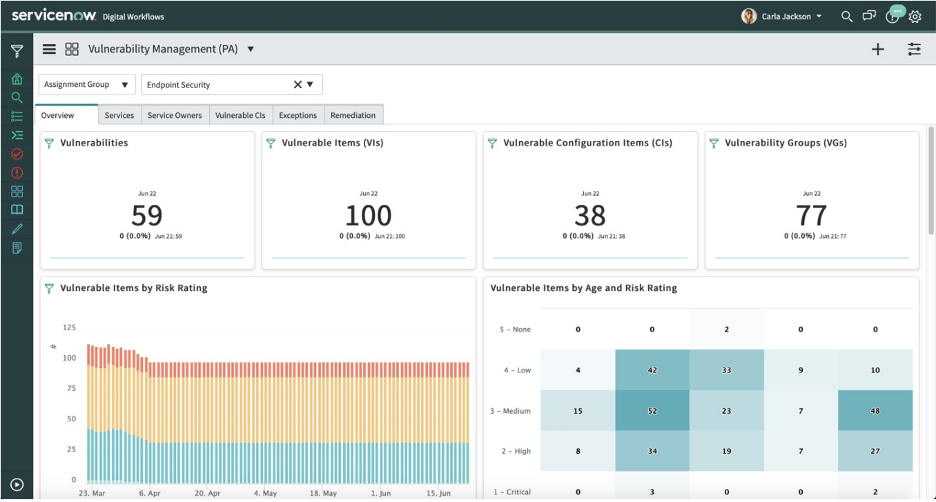
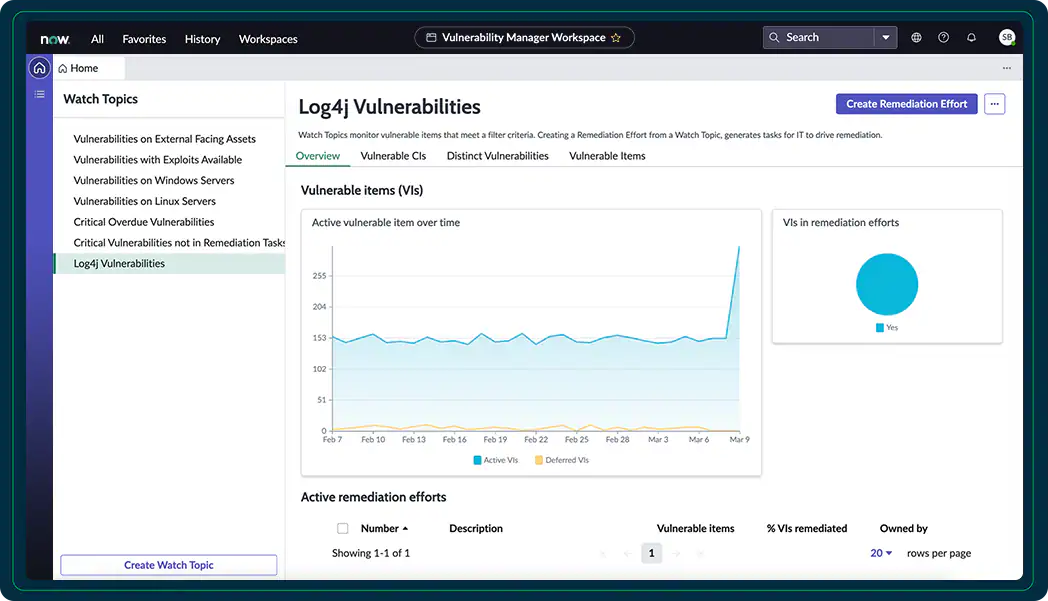
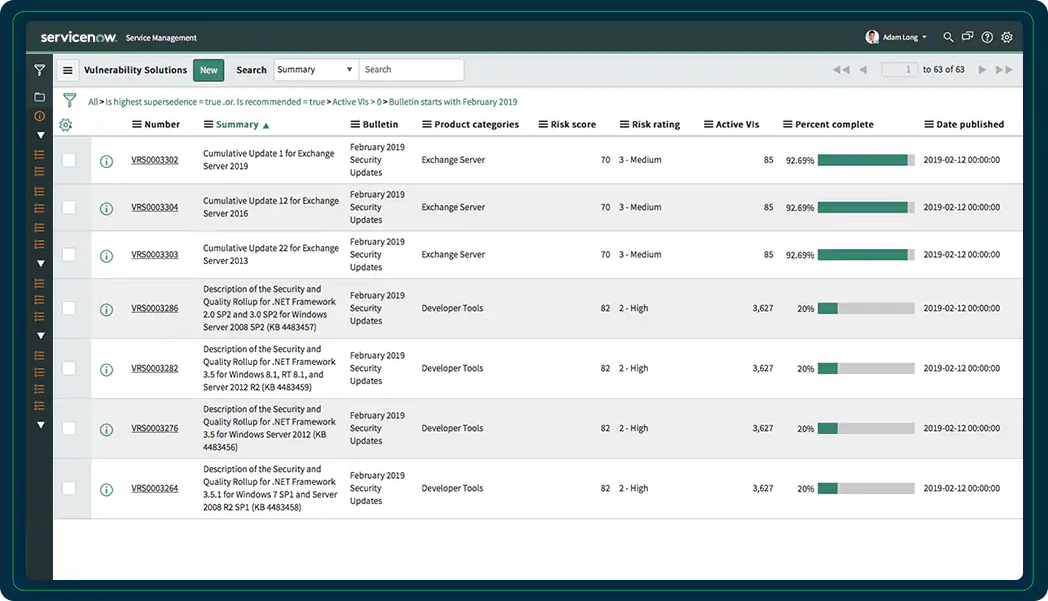
ServiceNow Vulnerability Response enables organizations to gain insights into prevalent and critical threats arising from external sources and their internal application developments. As a ServiceNow strategic partner, Aelum offers a tailored timeline for an industry-specific Vulnerability Management solution, leveraging ServiceNow Vulnerability Response. This solution encompasses various integrations with vulnerability scanners, configuration compliance, and threat intelligence solutions. Aelum utilizes ServiceNow’s CMDB and enterprise-wide workflow engine to facilitate seamless implementation and efficient management of the solution.
Intro
Organizations constantly need to innovate and adapt to meet customer demands and scale effectively. However, implementing new technologies can introduce vulnerabilities to IT infrastructure security.
For example, migrating to the cloud may expose organizations to external threats. Failing to assess security risks when introducing new elements like remote working setups can lead to a breakdown in the overall security strategy.
Hence, it’s essential to address vulnerabilities promptly, as critical threats may go unnoticed and have a significant impact on a business’s reputation and data security.
Breaches are becoming more severe, and cybercriminals are using advanced techniques like AI and ML to bypass traditional vulnerability response methods.
To stay ahead of these tactics and achieve a holistic approach to vulnerability response, a comprehensive solution that integrates security, risk, and IT components is crucial. Although challenging, ensuring complete efficiency in vulnerability response has never been more critical.
Why Security is a Big Concern for Organizations?
The abundance of vulnerabilities available for exploitation by malicious actors is undeniable. The potential consequences of a data breach, which encompass not only financial repercussions but also operational disturbances, erosion of customer trust, harm to brand image, and even possible legal consequences, underscore the criticality of identifying and addressing vulnerabilities.
A proficient vulnerability management system offers a crucial extra level of defense, empowering organizations to continuously oversee and rectify security weaknesses within their IT infrastructure.
Overview of Application Vulnerability Response
Application Vulnerability Response (AVR) is a crucial component of Vulnerability Response that focuses on Dynamic Application Security Testing (DAST) and Static Application Security Testing (SAST) data.
DAST scans are used to identify vulnerabilities in the behavior of the overall application, whereas SAST scans target vulnerabilities in the code itself. The key distinction is that SAST scans are conducted on non-compiled source code independently of any running application.
Note: Data from SAST, Software Composition Analysis (SCA), Interactive Application Security Testing (IAST), and PEN testing are not ingested and may result in differences between Veracode and Application Vulnerability Response.
Features
Application Vulnerability Response offers several key features:
- CI Lookup Rules: This feature automatically searches application data for matches in the Configuration Management Database (CMDB), ensuring accurate and efficient vulnerability identification.
- Assignment Rules: Automatically assign application vulnerabilities based on user groups, user group fields, and scripts, streamlining the vulnerability management process.
- Risk Calculators: Prioritize and rate the impact of Application Vulnerable Items (AVIs) using calculators, which can be based on any criteria through condition filters, allowing for effective risk assessment.
- Severity Mapping: Automatically calculate initial values for fields on application vulnerable items, including both source severity and normalized severity based on severity mapping. The severity is linked to the Common Weakness Enumeration (CWE) for standardized vulnerability classification.
- Remediation Target Rules: Define expected time frames for remediating application vulnerable items, helping organizations set clear goals for resolving vulnerabilities promptly.
- Reporting: Gain valuable insights into security posture and remediation trends, and identify the top 10 Applications or Business Units with the most critical AVIs. This feature provides comprehensive visibility to support informed decision-making and security improvement.
Use Cases of Application Vulnerability Response
DAST use cases include relating vulnerability scan results to CMDB configuration items (cmdb_ci) and associating DAST scan results with existing applications in the CMDB. It also involves storing DAST scan results for applications managed in systems other than ServiceNow® or if previous customizations have been made.
Similarly, SAST use cases involve relating scan results to CMDB configuration items and creating configuration items manually for source code repositories. Additionally, SAST scan results without a related Application Service can be stored.
Both types of scans are connected through the application release, which groups scanned vulnerability results on the scanner side. AVR utilizes this information during scan result import through the integration.
Best Practices to Utilize Application Vulnerability Response
Here is how you can make the most out of ServiceNow Vulnerability Response Application:
Start by Understanding Your Current Vulnerability Posture
The Application Vulnerability Response module can help you to assess your current vulnerability risks by providing you with a comprehensive view of all of your known vulnerabilities. This information can help you to prioritize your remediation efforts and to focus on the most critical risks.
Automate Your Vulnerability Management Processes
Manually managing application vulnerability is error-prone. ServiceNow’s Application Vulnerability Response can help you to automate many of your vulnerability management processes, such as:
- Vulnerability scanning
- Vulnerability prioritization
- Vulnerability remediation
This can save you time and effort, and it can help to ensure that your vulnerability management processes are consistent and efficient.
Make Use of Threat Intelligence
Businesses often face security issues due to a lack of visibility into their IT infrastructure, services, and solutions. Identifying vulnerabilities and responding to threats in real time becomes challenging for security and IT teams, as they spend significant time pinpointing the root causes behind these vulnerabilities.
ServiceNow Threat Intelligence comes to the rescue by leveraging artificial intelligence and machine learning to provide a reference point to the Structured Threat Information Expression (STIX) data. This technology aids in streamlining the process of identifying and addressing security threats effectively.
Integrate with Other Security Tools
It can be integrated with other security tools, such as vulnerability scanners, SIEMs, and incident management systems. This integration can help you to get a more comprehensive view of your security posture and to improve the efficiency of your security operations.
Use it to Improve Communication and Collaboration
Use the module to improve communication and collaboration between your security and IT teams. This can help to ensure that vulnerabilities are identified and remediated more quickly and efficiently.
Let the Experts Handle Your Application Vulnerability Response
Businesses face various technical challenges in vulnerability management, including incomplete asset inventory, the overwhelming scope of vulnerabilities, reliance on manual processes, lack of visibility into the attack surface, delayed remediation, and poor communication between security and IT teams.
Consultants like Aelum offer a valuable solution to these challenges by providing their expertise in vulnerability management and ServiceNow’s Application Vulnerability Response. They can streamline and automate vulnerability management processes, saving time and reducing errors.
With Aelum’s support, businesses can improve their security posture and gain peace of mind knowing their vulnerability management program is in capable hands, thus reducing the risk of potential attacks.